Threat Intelligence Report 2025
Latest cybersecurity threats you can’t ignore
Stealth intrusions are reaching the telecom core, DDoS floods hit multi‑terabit peaks within minutes, and cryptography requirements are accelerating.
See what’s changed, what’s at risk, and how the industry is fighting back.
Key resources

Report
Threat Intelligence Report 2025
Open the full report instantly in your browser

Infographic
Critical network security infographic 2025
A quick, visual summary of 2025’s threat patterns
What’s inside the report?
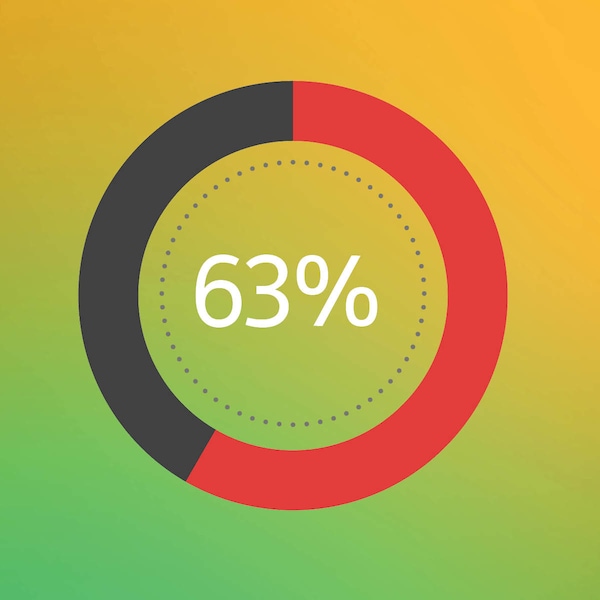
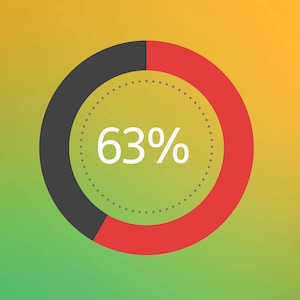
Stealthy campaigns targeting the telco core
Adversaries are shifting from opportunistic hits to coordinated, infrastructure-level campaigns. They blend into routine administration, using trusted tools and configuration drift to persist inside lawful interception paths, mobile core signaling, orchestration layers and subscriber databases.
Across network operators, 63% encountered at least one “living-off-the-land” campaign over the past 12 months, and almost a third saw four or more. When routine activity becomes the cover, the core becomes a hiding place.

DDoS attacks that are faster, stronger, and relentless
DDoS storms aren’t just big in terms of traffic volumes; when they happen, they are fast rising, like a tsunami. Peaks in the 5–10 Tbps range have become a daily norm and can occur in a very short time. 78% percent of DDoS attacks conclude within five minutes, and more than a third are completed in under two minutes.
Residential proxy networks with 100 million+ hijacked home devices and Mirai-descendant botnets like Eleven11 can unleash multi-terabit floods in a few minutes.
The report breaks down multi-vector patterns and shows how to design sub-60-second mitigation at the edge to keep traffic flowing.

Insider risk and hygiene gaps driving costly breaches
Nearly 60% of high-cost breaches in telecom stem from insider actions or mistakes, whether malicious or accidental. The report highlights that these incidents are often enabled by gaps in privilege management, credential misuse, and lack of behavioral monitoring. Real-world examples include contractors disabling multi-factor authentication, vendors reusing credentials, and even physical access being exploited to plant rogue devices.
76% of vulnerabilities are due to missing patches. Application flaws, weak passwords, and legacy systems widen the attack surface, making patching and monitoring essential.

Real-world case studies & field data
- Salt Typhoon and BPFDoor show how attackers can persist undetected for months or years, using device-level exploits and kernel implants that evade standard controls. These cases reveal how routine operations can mask long-dwell threats.
- Bite Latvija’s DDoS telemetry offers a real-world look at attack frequency and complexity, with thousands of multi-vector attacks per year, most peaking within minutes. Their experience underscores why sub-minute, automated enforcement is now essential for effective DDoS defense.
About Nokia’s Threat Intelligence Report
The Nokia Threat Intelligence Report brings together operational insights from NetGuard and Deepfield, real‑world data from Managed Security Services, research from Nokia Bell Labs, and expertise in cybersecurity consulting and quantum‑safe networking.
It is enriched with quantitative and qualitative input from 160 telecom security leaders worldwide, providing a nuanced, evidence‑based view of risks and responses.
You’ll find practical recommendations across threat detection and response, AI adoption, DDoS mitigation, regulatory compliance, and quantum readiness to help network operators strengthen resilience.
Actionable insights you’ll gain

Spot stealth attacks in the telco core
Practical ways to baseline privileged behavior and surface “living off the land” activity in lawful interception, subscriber data, and core control systems.

Mitigate short, high‑volume DDoS
Design sub‑minute detection and edge mitigation for multi vector, multi terabit DDoS campaigns that peak faster than manual playbooks can react.

Shrink insider and vendor risk
Close high impact gaps with least privilege, just-in-time access, and continuous third party validation mapped to telco realities.

Achieve crypto agility, not crypto fragility
Automate certificate lifecycles now and plan post quantum migration before shortened validity windows trigger outages.

Automate zero-day threat detection
Deploy telecom-aware, ML-based anomaly detection to spot novel threats that traditional tools miss.

Let AI hunt threats for you
Leverage AI to flag subtle, fast-moving attacks, predict attack chains, and auto-trigger playbooks.
Who benefits most from reading?
Security leaders
Understand the latest tactics attackers use to target telecom networks and get practical recommendations to reduce risk and improve response.
Technical teams
Find actionable guidance for detecting stealthy intrusions, responding to DDoS attacks, and closing gaps caused by insider mistakes or poor hygiene.
Risk and compliance professionals
Stay up to date on regulatory changes, cryptography requirements, and operational risks that can lead to outages or penalties.
Threat Intelligence Report 2025
Expert perspectives
FAQs and next steps
For the first time, the report pairs Nokia’s operational data and research with a global survey of 160 telecom security leaders, adding fresh, operator‑level insights to the analysis. It also includes new real‑world case studies and updated guidance on DDoS, stealthy intrusions, and cryptography timelines.
No. The infographic gives a fast visual summary. The full report adds technical deep dives, operator quotes, case studies, and detailed recommendations
It’s written for both executives and practitioners. You’ll find board level framing, plus specific controls and architecture patterns for SOC, transport/IP, core/cloud, and compliance teams.
The infographic summarizes key findings. For detailed analysis and recommendations, download the full report.
Security leaders, technical teams, and risk or compliance professionals at telecom operators and service providers.
Related topics

Cybersecurity
Industry leading end-to-end 5G security.

Quantum-safe networks
Making critical infrastructure quantum-safe.
Related solutions and products
Solution
XDR Security
Cloud-native Extended Detection and Response
Product
Deepfield Defender
Next-gen, big data and AI-driven DDoS detection and mitigation solution
Topic
DDoS security
Defend your network against botnets and application-layer attacks with an AI-driven DDoS security for fast and accurate detection and real-time mitigation
Service
Cybersecurity consulting
Leading holistic security advisories for critical networks
Solution
IP network security
Protect your network with multi-layered embedded IP network security
Learn more about threat intelligence and security

Blog

Blog

Blog
Video
Nokia 6G Livestream: Security Blueprint
Blog

Brochure
Article

Solution brief
Latest news
Ready to talk?
Please complete the form below.
The form is loading, please wait...
Thank you. We have received your inquiry. Please continue browsing.